Monitoring of compromised data
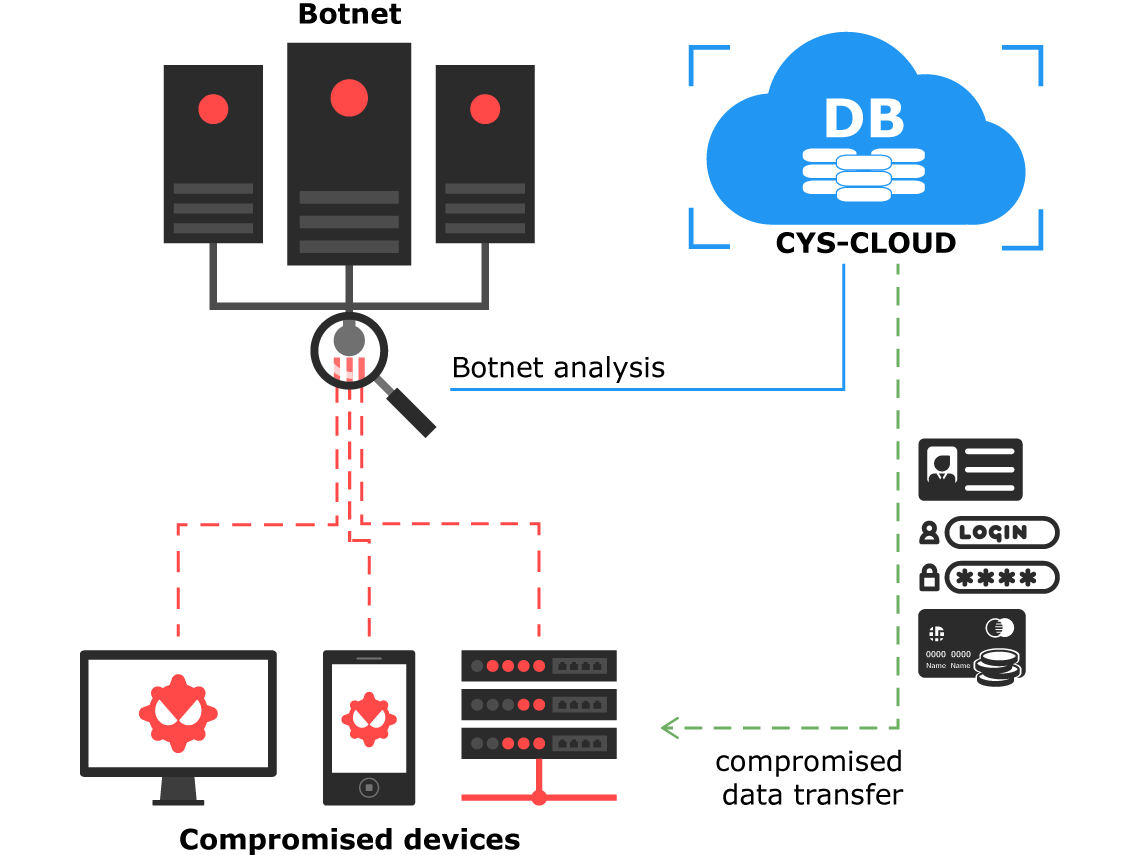
CyS Centrum provides monitoring of botnets worldwide on a regular basis. We focus on botnets that may be used to exfiltrate sensitive data (logins, passwords, keys and certificates, PANs, CVVs, personally identifiable information), steal money and provide remote covert management of infected devices. Dut to unique and trusted relationship with competent organizations around the globe, recognizing the transnational nature of cyber-threats, we organize effective mutual cooperation aimed at incident response at the international level. All this enables us to know in advance "who", "when" and "where" will lauch the attack, thus giving CyS Centrum the unique advantage in addressing threats proactively (during the initial stages of an attack).
Detection of compromised devices used by financial institutions and their customers
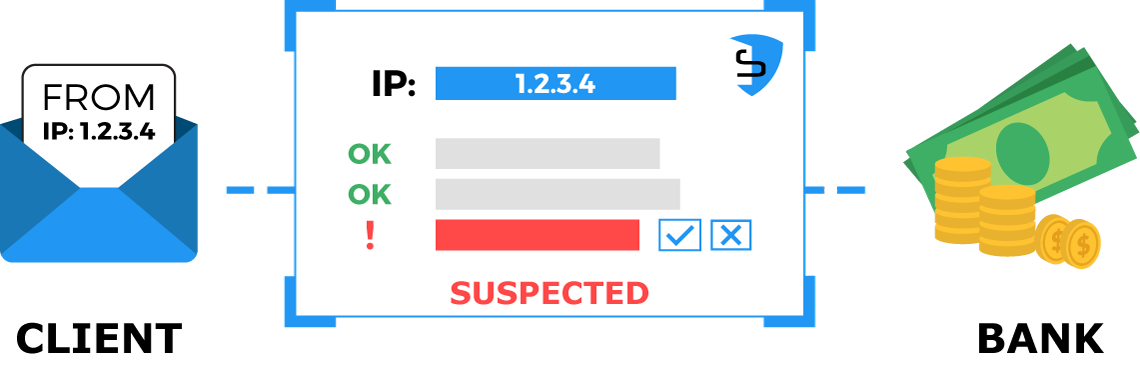
CyS Centrum’s technical solutions and commercial agreements with partners (from the global InfoSec community) give us an opportunity to get and process real-time information about compromised IP-addresses from the entire Ukrainian cyber-space. This enables us to estimate “reputation” of each and every Ukrainian IP-address and determine, whether it’s used by a botnet, infected with malware, participating in DDoS or other attacks, or used for scanning/spamming purposes. It's also possible to detect "client-side" infections by checking clients IP-addresses through our data sets. This service may be implemented in one of two ways: as an automated control system (requires integration to the bank’s infrastructure) or as an outsourced feature (where CyS Centrum takes responsibility to provide regular reputation checks and appropriate reporting).