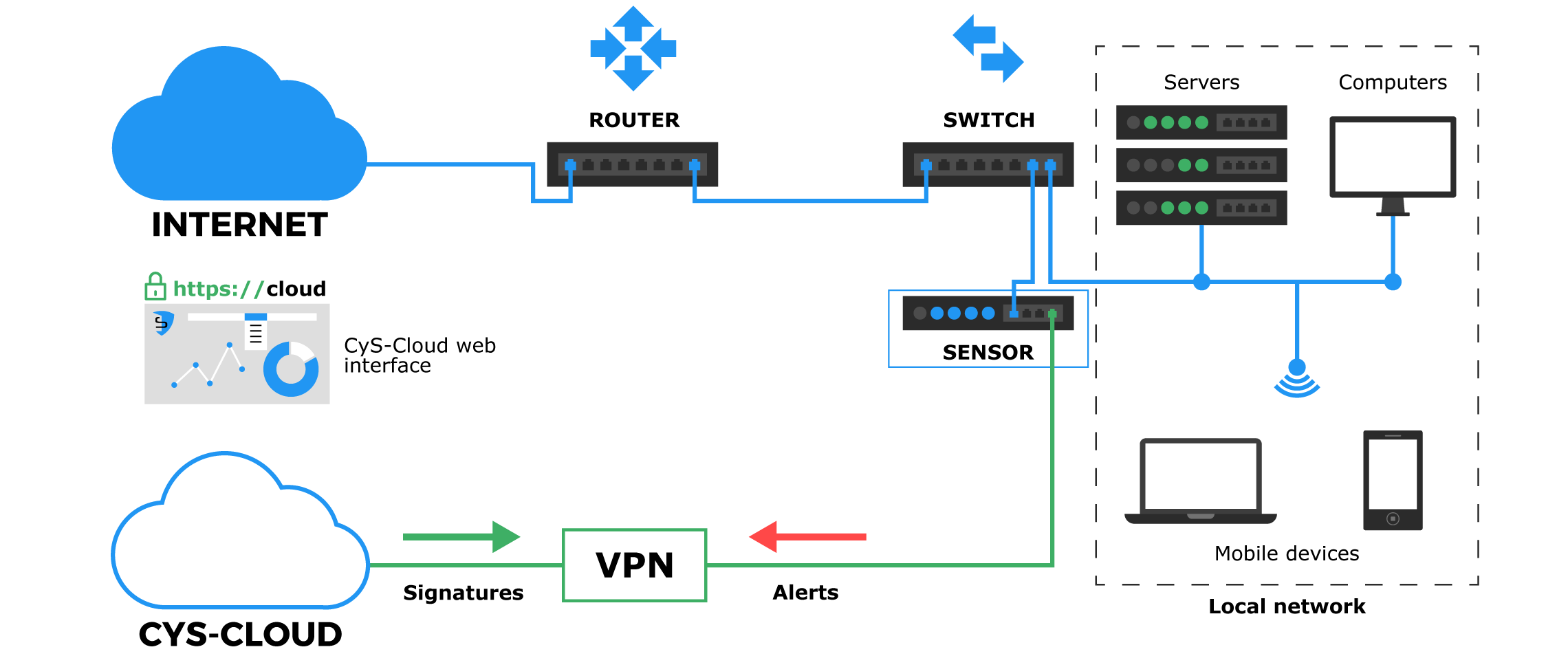
Monitoring of information flow … why?
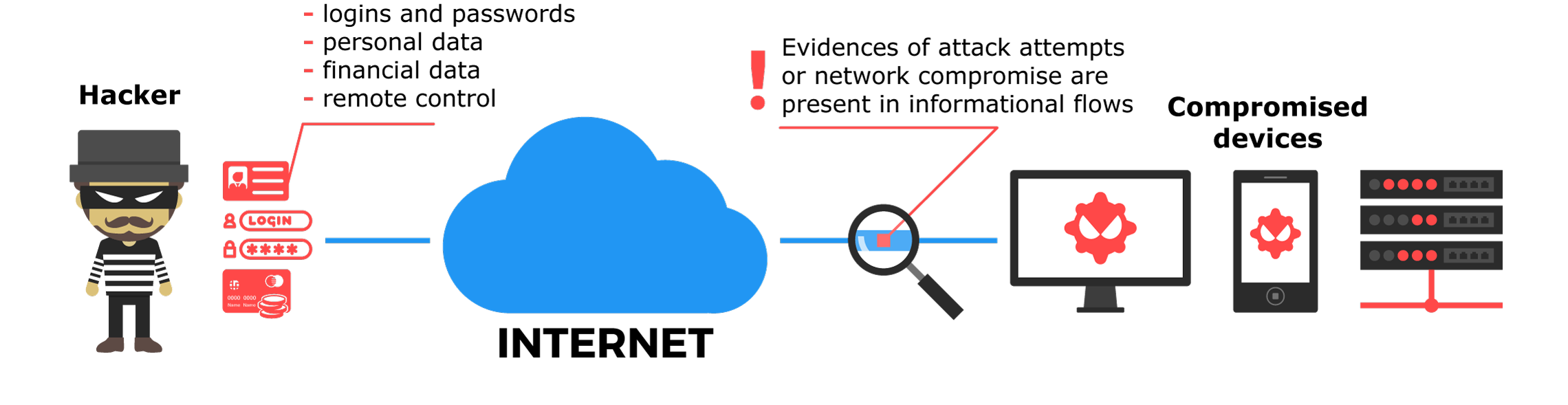
Confidential data is one of the goals pursued by hackers while attacking a network. A successful attack means compromise of sensitive data such as: logins, passwords, certificates, emails, commercial secrets and/or unauthorized system access, which enables an adversary to manage a remotely hacked system, disrupt its functionality or carry out surveillance. Additionally, it’s vital to understand that there is a variety of points of compromise: from laptop to gadget, used within organization’s wireless network. Meanwhile, accountants and system administrator’s computers are being targeted on a more frequent basis.